Enhancing Security in an Open Source Password Manager
Implementing a new breakthrough cyber security technology created by the Tide Foundation.
EDUCATION


When it comes to the integrity and confidentiality of sensitive data, there's no room for compromise.
In the realm of cybersecurity, safeguarding information against unauthorized access is paramount. It's within this context that this project takes place.
During my internship with Tide, (see tide.org) I had the chance to gain direct help in implementing their new API, Heimdall, Which offers developers a unique opportunity to implement a new encryption paradigm characterized by its trustless, fully-verifiable, decentralized nature.
Heimdall's Decentralized Nature
At its core, Heimdall employs a decentralized system where cryptographic keys are created and used in a fragmented state. Unlike traditional encryption methods where a complete key is assembled when used and made vulnerable, Heimdall ensures that the key remains fragmented at all times therefore, forever unattainable. Forever secret. This fragmentation also guarantees that no single entity, not even those hosting key fragments, possesses any knowledge of the full key's composition or access to it.
This approach allows for the hosting of key fragments across diverse operators, platforms and locations. This flexibility not only enhances scalability but also mitigates risks associated with centralized key management, providing added resilience against security breaches even by the most priviledged users.
So what is Buttercup?
Buttercup is an free opensource password manager and is best described by their statement on buttercup.pw, which is to say "a beautifully-simple password manager designed to help manage your credentials. Buttercup uses very strong encryption to protect your sensitive details under a single master password" ("Buttercup.pw, " n.d.).
Something that is very refreshing about buttercup is the principle that allows a user to have complete control over their vault and how it's stored and their use of AES-256 a well known and well tested encryption algorithm, to ensure a users security.
How I handled the implementation of Heimdall
In practical terms, Buttercup users now have access to a new vault type: the Tide vault. This vault leverages Heimdall, accessing the Tide vault is streamlined for user convenience while maintaining robust security measures. The Tide vault is stored on an online server but is encrypted using Heimdall, ensuring the confidentiality of sensitive data. Here's how it works:
Simple Setup: Creating or accessing a Tide vault is as easy as a few clicks. Users can initiate a new vault creation process, select the Tide Vault option, and proceed to log in or create a Tide Account.
Seamless Access: Once logged in, users gain immediate access to their Tide vault. For new users, the vault is created seamlessly. For existing users, their vault is loaded, ready for use.
Enhanced Security: Despite the simplicity of the login process, security remains uncompromising. Heimdall's encryption methodology ensures that the strength of the Tide Account password doesn't impact the encryption's robustness. Moreover, the login process incorporates brute force protections, thwarting unauthorized access attempts.
Flexibility and Transparency: While the Tide vault is hosted on an online server, users maintain the flexibility to host it themselves. The open-source nature of the code allows users to access the server code, facilitating self-hosting. By simply adjusting the connection address when adding a Tide vault, users can seamlessly transition to self-hosting, preserving control over their data.
My hope is that this implementation strikes a balance between user-friendliness and stringent security measures. By leveraging Heimdall’s encryption and integrating the Tide Account for authentication, users can enjoy a hassle-free, ubiquitous experience without compromising on data protection. Moreover, the option for self-hosting provides added control, allowing further control of a user’s information.
Potential Improvements
In the project, I honestly implemented the bare basics of Heimdall’s capabilities, while a lot of my time was spent understanding TypeScript, Electron and improving my JavaScript and knowledge of NPM.
A feature that Heimdall enables is a secure method to share fields of information, by allowing the specific users delegated access to specific group folders from Tide Vaults, allowing say a family member to share specific passwords or even entire password folders in a secure manner! Below I've posted the encrypt function, you'll notice the fieldData variable, these fields can be decrypted by different tide accounts if given the correct authorization by the owner of the data.
The current implementation simply encrypts the entire vault as a blob of data under 'vaultdata', however further improvements could be made, for example creating a field for each folder, and encrypting the folders contents as a whole, or simply encrypting every password under its own field.
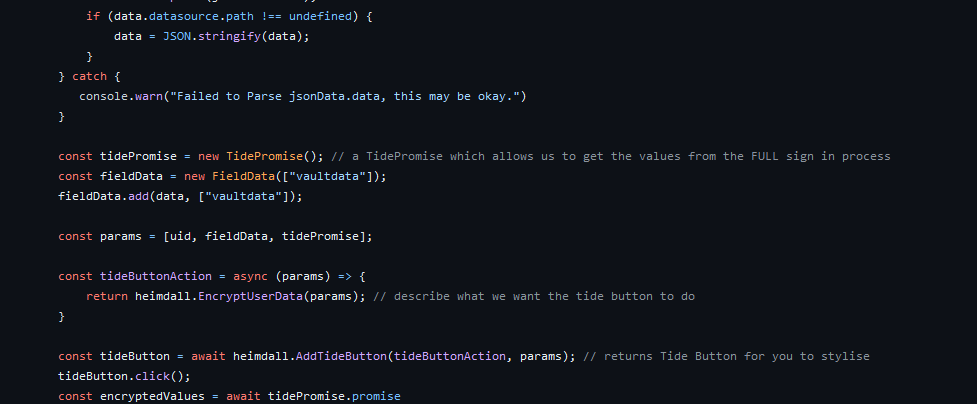
Final thoughts and Conclusion
Integrating Heimdall has significantly bolstered Buttercup's security, surpassing any competitive alternative, ensuring parity with existing options while enhancing protection for users' sensitive data.
In traditional Buttercup Vaults, security relies solely on a Master Password, with unlimited unlock attempts allowed. However, Tide vaults utilize Heimdall's encryption, rendering brute force attacks ineffective and providing an extra layer of protection.
It's important to note that both Buttercup and Tide vaults utilize the same AES-256 encryption algorithm. However, the key difference lies in the key creation and usage process. While traditional Buttercup Vaults rely on the Master Password system, Heimdall employs a comprehensive process to generate a unique, decentralized and forever secret key for each platform linked to a user’s Tide Account.
I'd like to extend my sincere gratitude to my dedicated team members, Amal Saju Kalarickal and Impana Vasudev, whose invaluable contributions were pivotal to the success of this project.
Furthermore, I wish to extend my gratitude to the Tide Foundation for affording me the invaluable opportunity to intern with their esteemed organization. I would also like to offer a heartfelt acknowledgment to Yuval Hertzog for his meticulous proofreading of this post.
Special thanks to Perry Mitchell, for going out of his way to help provide insights into his application and answer questions my team and I had in regards to the layout and method the repositories worked together and how the application functioned.
If you're interested in the original application, buttercup, you can find it here, and for those interested in delving deeper into the branch that my team and I created, you can find the primary repository here.
This experience has been truly enriching and rewarding, and for that, I am sincerely thankful.


